

Most DNS queries are UDP.
I’d do a modified scream test and change old.domain to something like 1.2.3.4. Then run sudo netstat or ss with -tpn, grepping for 1.2.3.4.
Or something like grep -r old.domain /etc.


Most DNS queries are UDP.
I’d do a modified scream test and change old.domain to something like 1.2.3.4. Then run sudo netstat or ss with -tpn, grepping for 1.2.3.4.
Or something like grep -r old.domain /etc.
Yep, that would work fine for the first line of defense. Eventually, you can expand it to copy, replicate, or drive swap the onprem backups offsite somewhere (e.g., cloud, office, or family member) if you want to protect your data from site loss (e.g., house fire).
The only thing missing is a good backup.
If you are storing anything important – especially Immich and Vaultwarden data – you should have a good offsite protection strategy. And even the HASS config should be backed up with versioning because rebuilding from scratch could be painful once you get deep into it.
I’ll let others chime in on possible good backup options because I use Veeam and Azure, which really isn’t in the spirit of this community, and I’d be interested in good open source options myself.
Also, RAID (mirroring) is NOT a backup.


The easiest way that doesn’t affect the main network would be to use a travel router. Its WAN IP would be the private IP it gets from the main network (over wireless since that’s your only option). And it would NAT your network onto that IP and then you can do whatever you want on your network.
I’m not sure if that Mikrotik router will do this but it might. You basically need something that can connect to an SSID and use that interface as its WAN interface. The wireless factor here is really limiting your choices. If you had a wired uplink to the main network you could use any router/gateway/firewall you wanted. You could also use an AP in bridge mode to connect to the main network’s SSID and wire it to the WAN port of any router of your choice.
You don’t really need to use VLANs to separate your network from the main network unless you want to share any of the same layer 2 segments (basically wired Ethernet) while keeping it isolated. But it doesn’t really sound like that applies in your scenario. Of course using VLANs within your network would still make sense if that applies (for example, to separate your server traffic from your IoT traffic).


Yep that’s how I have Syncthing set up. All global and local discovery disabled, no firewall ports open on the clients, no broadcasting, no relay servers. Just syncing through a central server which maintains versioning and where the backups run. Works like a charm.


Not that it’s my first recommendation for security reasons, and I would never do this in prod, but you can just add the self-signed cert to the local trusted root CA store and it should work fine. No reg changes needed.
If you do this, put it in the store of the user running the client, not LocalMachine. Then you just need to make sure you connect as something in the cert’s SAN list. An IP might work (don’t know since I never try to put IPs in the SAN list), but just use a hosts entry if you can’t modify local DNS.
Edit: after reading the full OP post (sorry), I don’t think it’s necessarily the self-signed cert. If the browser is connecting with https:// and presenting a basic auth prompt, then https is working. It almost sounds like there is a 301/302 redirect back to http after login. Check the Network tab of the browser’s dev pane (F12) to see what is going on.


most of those drinks are specifically designed with the ice in mind
Citation Needed
An SSO-like payment system with tracking and revocation is a great idea and would be amazing for us consumers. I’m just not holding my breath waiting for the corpos to implement it.
While nowhere near perfect (far from it, really), as long as the sites you are shopping on are PCI-compliant (most should be), you don’t have to worry too much about a compromised site leaking your payment details for use elsewhere.
Basically just use a password manager and don’t worry about saving credit card (NOT debit card) details in the site as long as they aren’t extra-sketchy.
Same here. Sometimes the same/next day shipping can help in an emergency, but otherwise it’s local if possible, or direct from the vendor if not.
Amazon’s shipping has declined and everyone else’s has caught up to the point it’s not much of a difference anymore.


This is like the epitome of the XY Problem.


Holy shit, I remember being excited for 2.4 because of iptables. That was over twenty years ago.


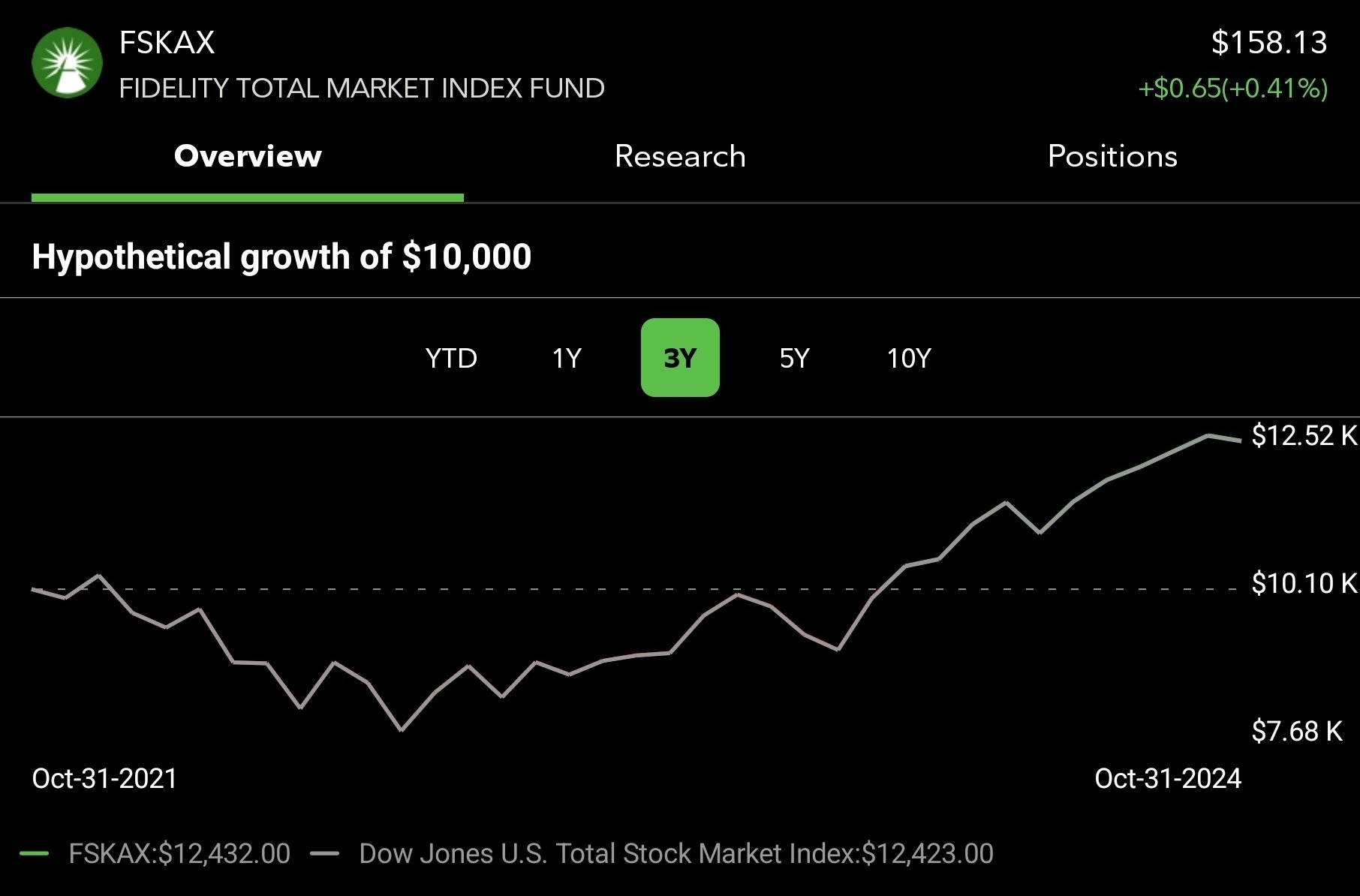
Yeah, this is FSKAX over 3 years. I have a lot of my portfolio in it and it does well. It’s up 24% over that period.


Use a Chromium browser to inspect the cert.
If anyone knows how to get Firefox to show a bad cert before loading the page, I’d love to know.


Assuming you’re the one adding HSTS, you’ll have to inspect the cert and/or view the content that is getting returned. On desktop Chromium you can type “thisisunsafe” to load a page even with HSTS. Not sure how to do it on mobile FF.
Would seem weird for it to be intercepting your domain’s traffic but not the rest of the internet.
Edit: just noticed you’re not even loading an SSL page. Are you using https in the URL?
If you’re sure you’ve got a DNS entry for the Pihole FQDN pointing at Traefik, open the dev panel in your browser (F12), switch it to the Network tab, and visit the pihole URL.
See if you get anything back and especially take note of the HTTP status codes.
Can you see the router and service in the Traefik dashboard and do they show any errors there?
I think you’re close.
You need to change service: pihole-rtr to service: pihole-svc.
Do I have to redefine all of the same information I did in my Traefik yml but in this separate config.yml?
No, you just need to reference it like you have. Define once, reference many.
No worries for the question. It’s not terribly intuitive.
The configs live on the Traefik server. In my static traefik.yml config I have the following providers section, which adds the file provider in addition to the docker provider which you likely already have:
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
file:
directory: /config
watch: true
And in the /config folder mapped into the Traefik container I have several files for services external to docker. You can combine them or keep them separate since the watch: true setting tells it to read in all files (and it’s near instant when you create them, no need to restart Traefik).
Here is my homeassistant.yml in that folder (I have a separate VM running HASS outside of Docker/Traefik):
http:
routers:
homeassistant-rtr:
entryPoints:
- https
service: homeassistant-svc
rule: "Host(`home.example.com`)"
tls:
certResolver: examplecom-dns
services:
homeassistant-svc:
loadBalancer:
servers:
- url: "http://hass1.internal.local:8123"
Hope this helps!
It’s unlikely since it uses the field ID and not the text, so it wouldn’t know which question went with which answer.
It’s so rarely needed to actually use these anyway, that it’s a non-issue IMO. You should never opt to use security questions as they are terrible from a security standpoint. This is just for when they are required by stupid websites.